Security Insights
Latest trends in cybersecurity, compliance updates, and strategic analysis for decision makers.
FEATURED INTELLIGENCE
Security Compliance Automation: The Consultant's Guide
Moving beyond the "SOC 2 in weeks" hype. A deep dive into decision factors, hidden risks, and scaling paths for compliance automation.
The Illusion of Control: Why Security Tool Consolidation Often Increases Risk
Consolidating your security stack promises efficiency, but often delivers fragility. A deep dive into the hidden costs of "Single Pane of Glass" promises.
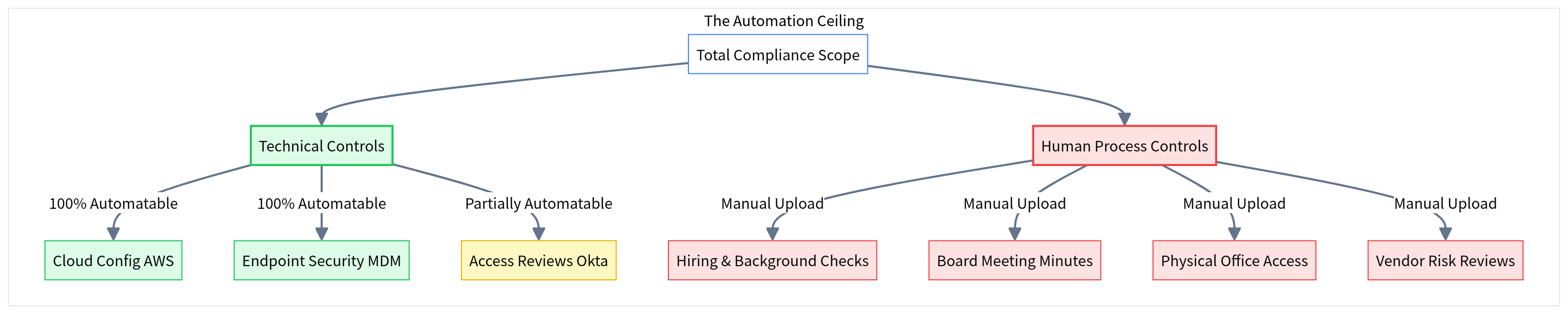
The 'Human Evidence' Gap: Why Automation Hits a Ceiling
Don't believe the '100% Automated' hype. Why critical SOC 2 and ISO 27001 controls still require manual screenshots, PDFs, and human workflows.
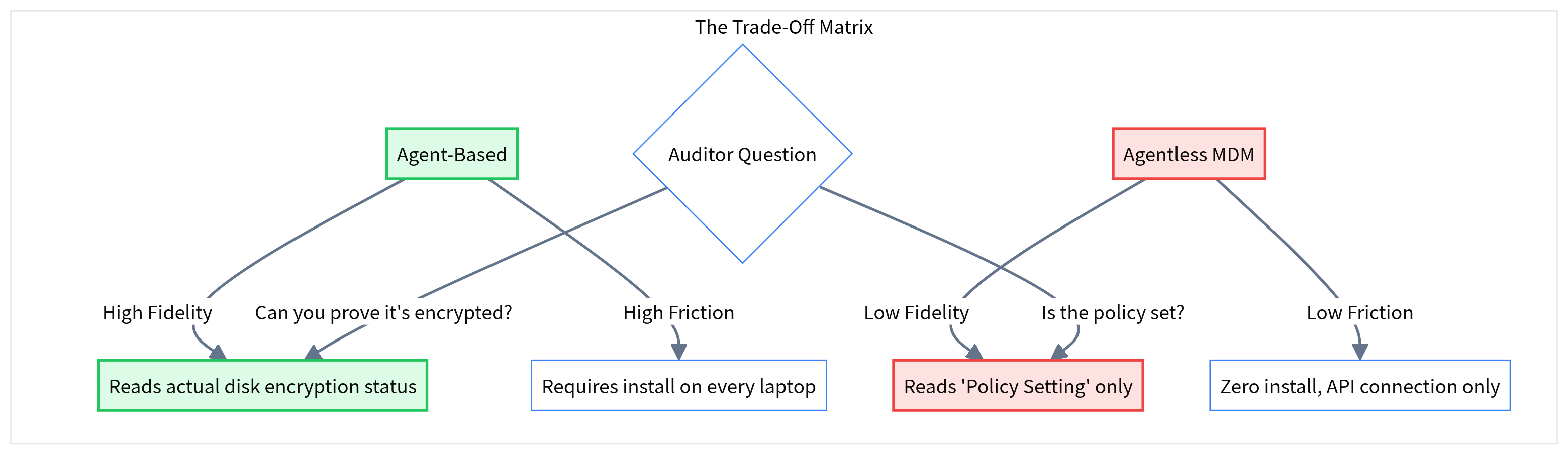
The 'Agentless' Blind Spot: Speed vs. Evidence Depth
Why 'Zero Deployment' can mean zero evidence. Understanding the critical trade-off between MDM-based scanning and agent-based reality checks.
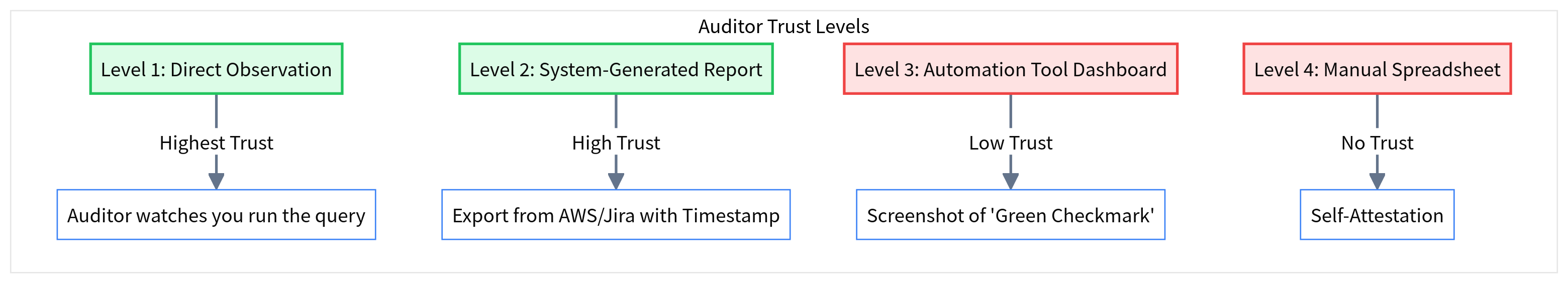
The 'Auditor Acceptance' Risk: Will Your Evidence Pass?
Why Big 4 auditors often reject automated evidence. A guide to IPE (Information Provided by the Entity) and avoiding the 'black box' trap.
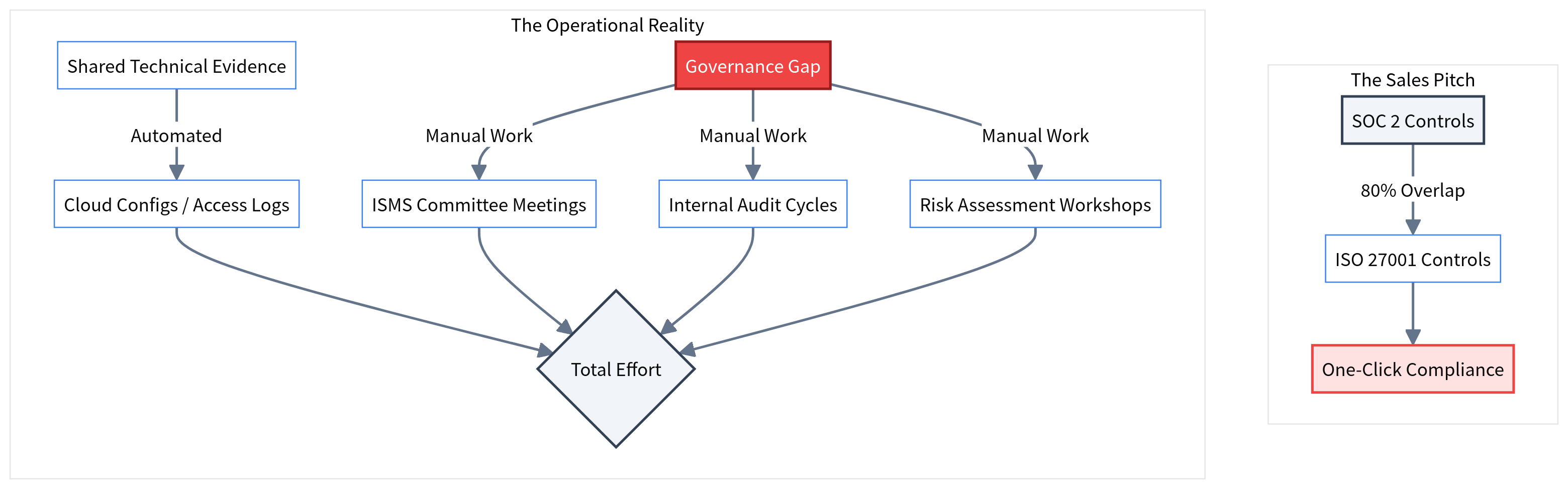
The 'Map Once, Comply Everywhere' Myth
Deconstructing the sales pitch that adding ISO 27001 to SOC 2 is just a 'one-click' upgrade. The hidden governance gap explained.
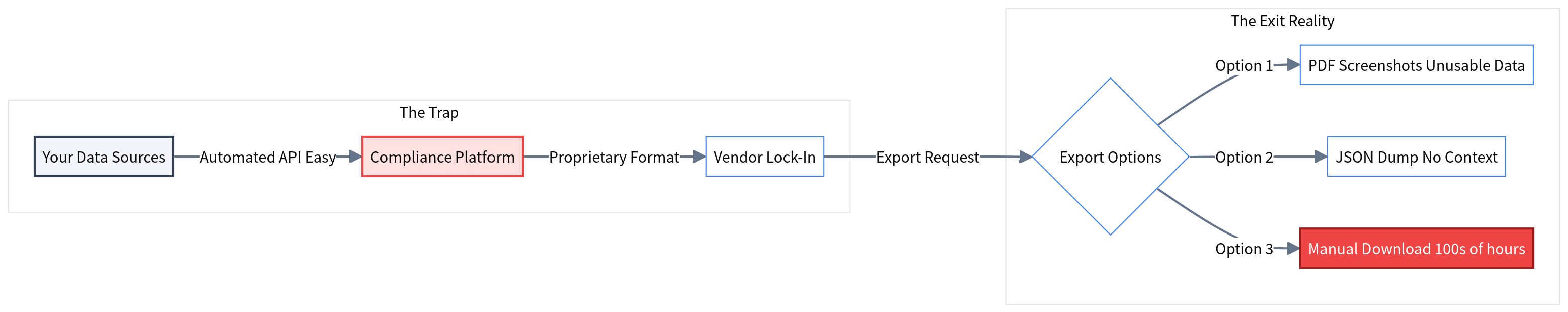
The 'Evidence Jail' Problem: Data Portability Traps
Why easy ingestion often masks difficult extraction. How to avoid vendor lock-in and ensure you own your audit history.
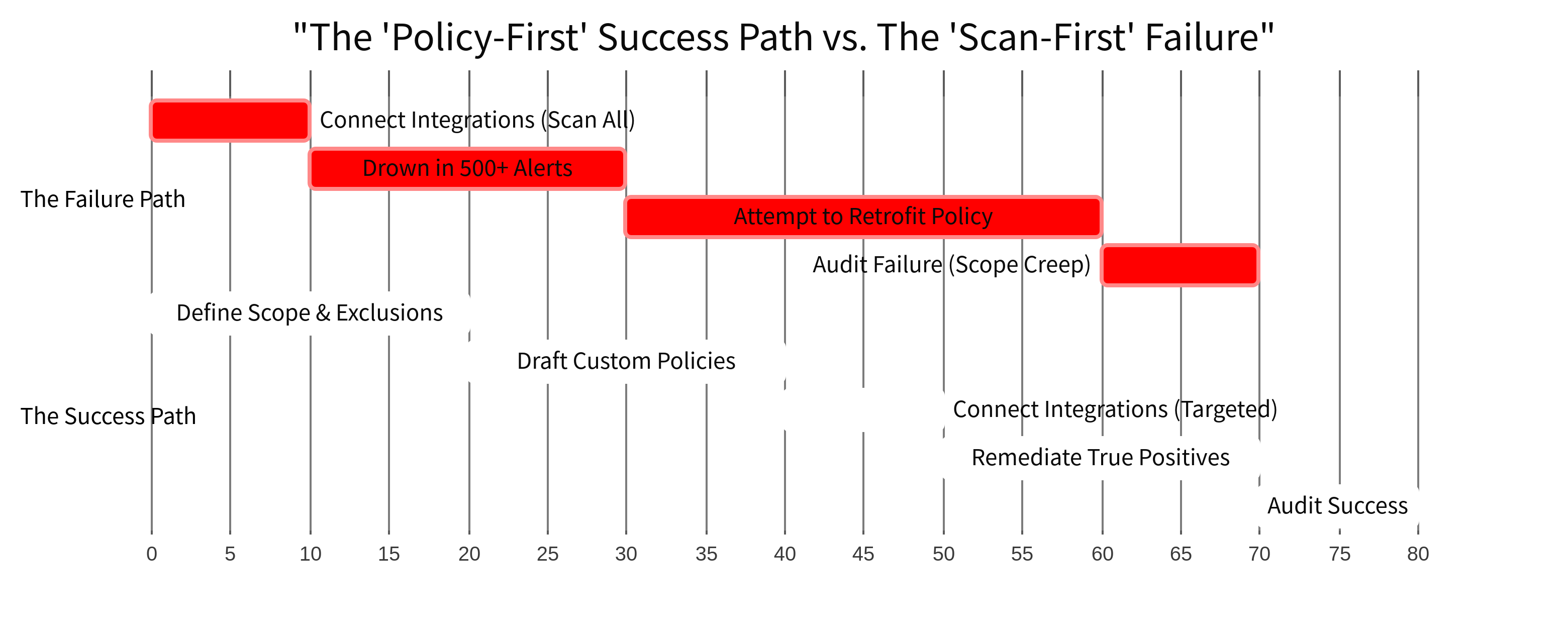
The 'Policy-First' Implementation Trap
Why scanning everything before defining scope leads to alert fatigue. The case for a 'Scope-First' approach to compliance automation.
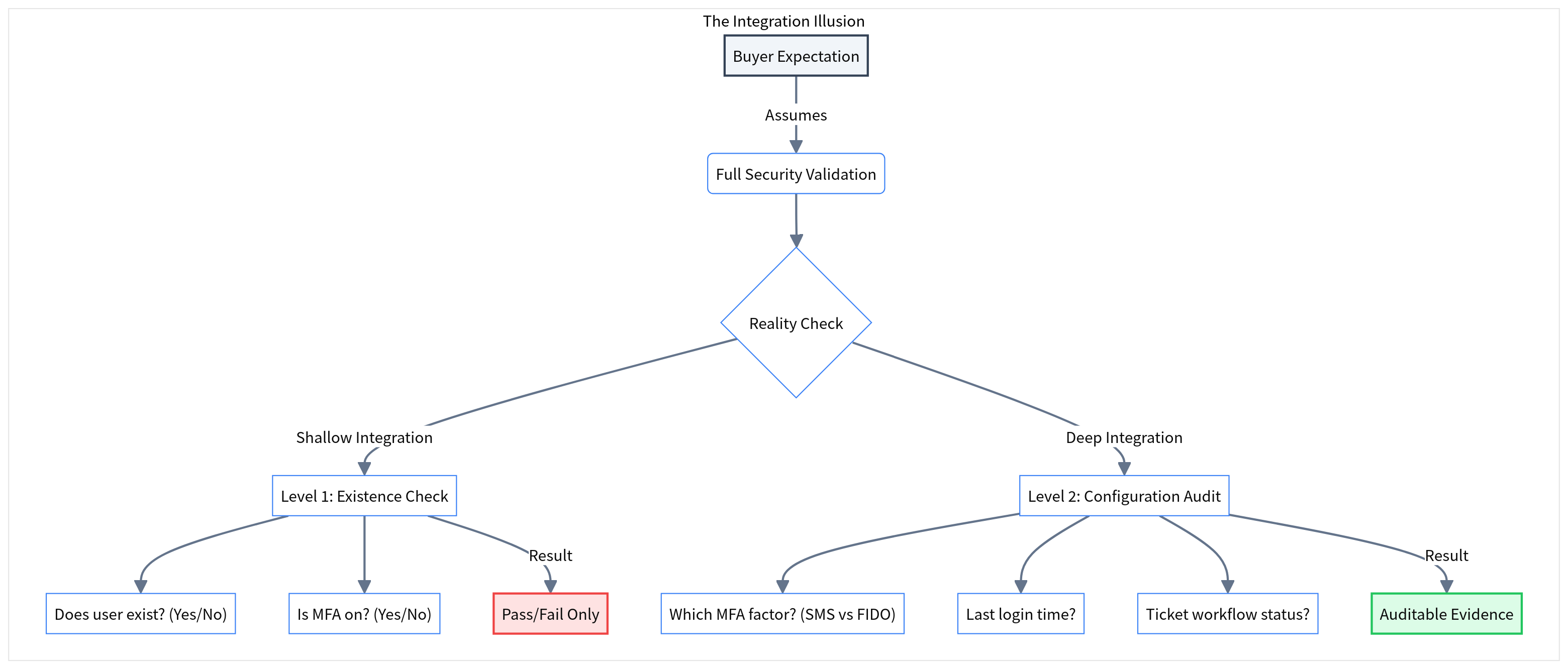
The Integration Depth Illusion
Not all 'Jira Integrations' are created equal. Why shallow API connections fail to provide audit-ready evidence.
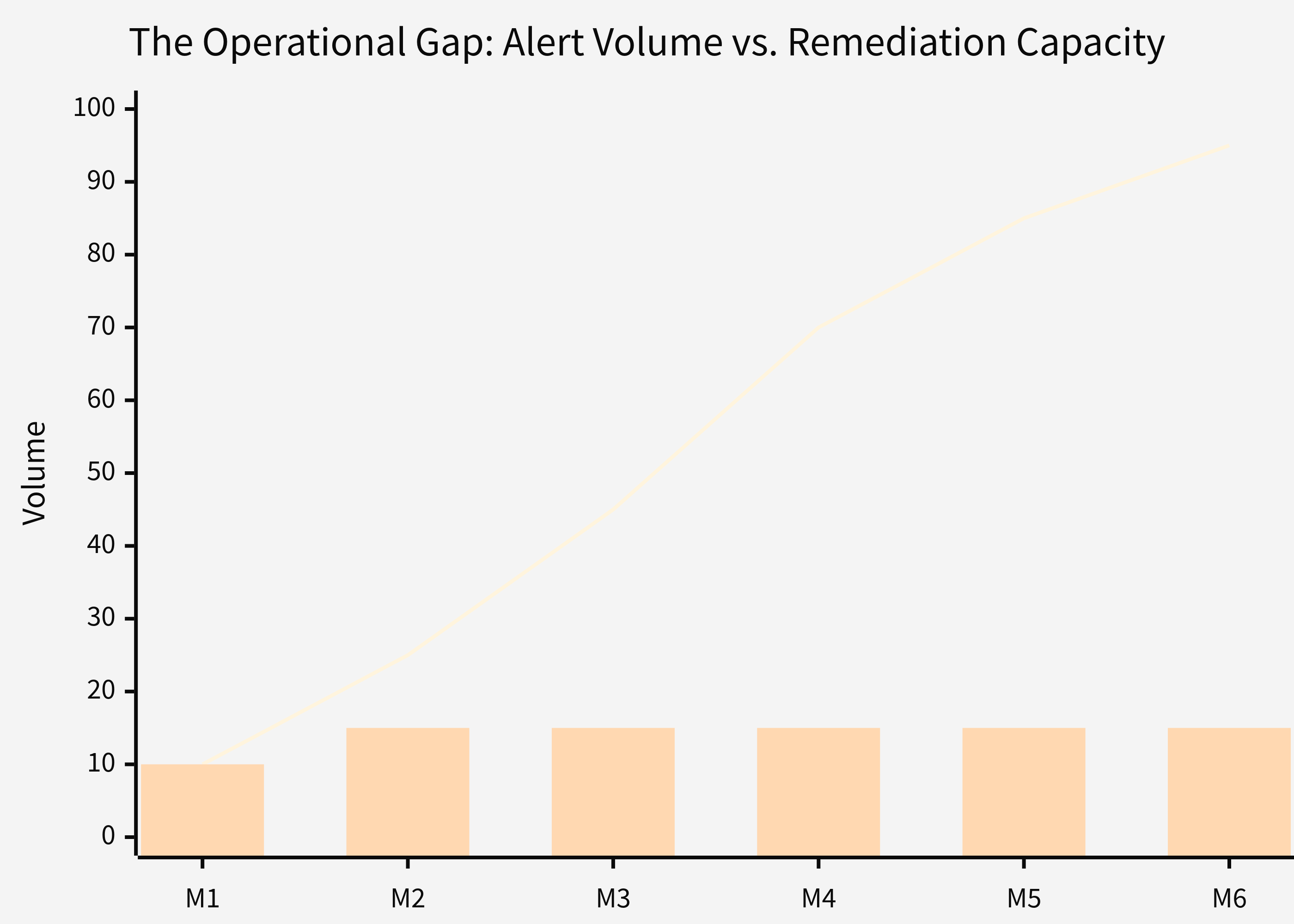
The Operational Reality of Continuous Monitoring
Buying a tool is easy; running it is hard. Addressing the 'Day 2' reality of remediation fatigue and operational overhead.

The Rise of Identity-Based Attacks in 2024
Why traditional perimeter defense is failing and how Identity Threat Detection and Response (ITDR) is becoming the new standard.

SOC 2 vs. ISO 27001: Which One First?
A strategic guide for startups deciding between the two major compliance frameworks based on market goals and resource constraints.

Zero Trust Architecture: Beyond the Buzzword
Deconstructing NIST 800-207. Practical steps to implement Zero Trust principles without disrupting business operations.

Vendor Risk Management in the AI Era
How to assess third-party AI tools for data privacy risks and ensure your supply chain remains secure.

Cloud Security Posture Management (CSPM) Explained
Automating the detection of misconfigurations in AWS, Azure, and GCP environments.

The Economics of Ransomware Defense
Analyzing the cost-benefit ratio of cyber insurance vs. proactive defense investments.