There is a seductive button in every compliance platform called "Connect AWS."
It takes 30 seconds. You click it, authorize the role, and suddenly the tool is scanning your entire cloud infrastructure. It feels like progress.
This is usually a fatal mistake.
By connecting first and scoping later, you have implicitly told the tool: "Everything in this account is in scope for SOC 2." The tool will dutifully report that your dev-sandbox, your deprecated prototype, and your intern's playground are all "failing critical controls."
The "Default Policy" Problem
Vendor platforms come with "Best Practice" policies enabled by default. These are designed to be universally applicable, which means they are universally strict.
For example, the default policy might require "Multi-Factor Authentication (MFA) on all user accounts."
In reality, your organization might have Service Accounts (non-human users) that technically cannot have MFA but are secured via IP whitelisting.
If you scan before you define your policy exception for Service Accounts, you wake up to 50 "Critical Failures." Your team panics. You spend three weeks explaining to the tool why these are exceptions.
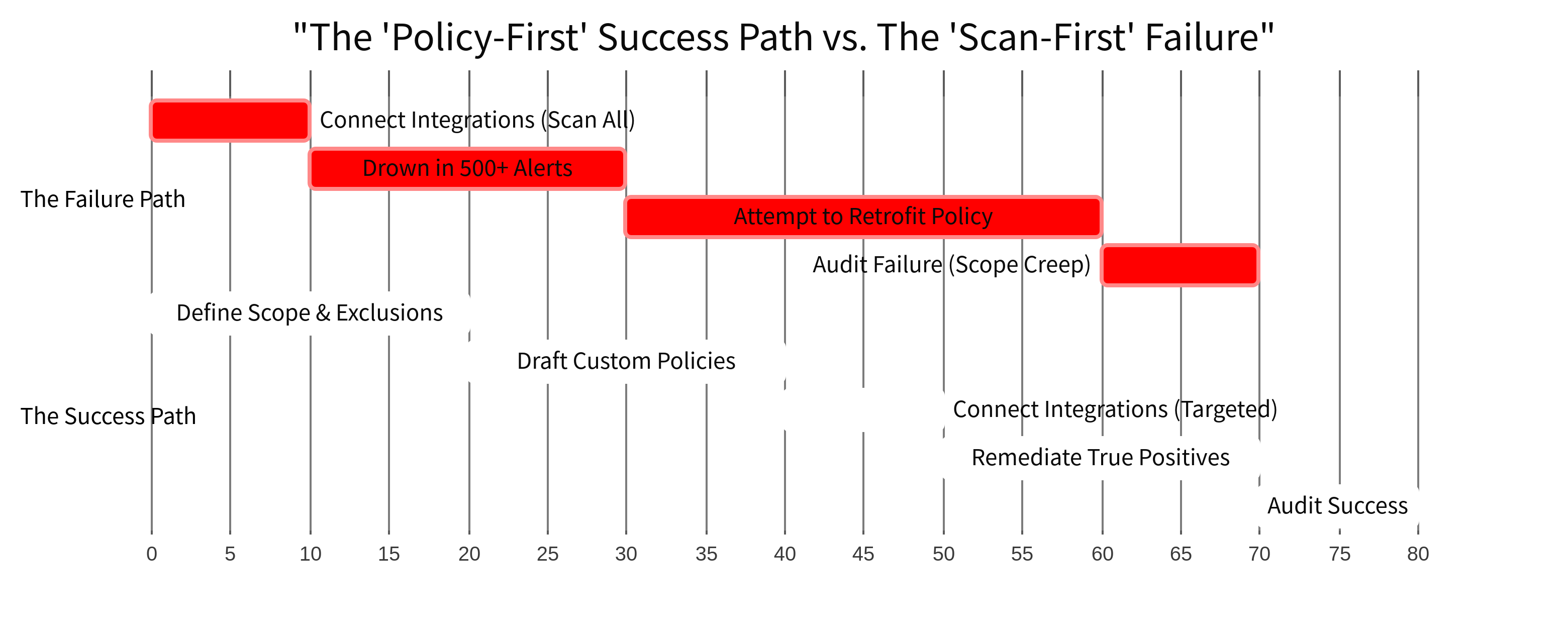
The Correct Order of Operations
To avoid the "Sea of Red," you must invert the typical onboarding flow.
- Define the Scope Boundary: Which AWS accounts matter? Which repositories contain production code? Write this down outside the tool.
- Draft the "Paper" Policy: Decide your stance on password rotation, laptop encryption, and vendor reviews.
- Configure the Tool's Logic: Go into the settings and disable the checks that don't match your policy. (e.g., If you don't do quarterly performance reviews, turn off that check).
- Connect the Integrations: Only now do you turn on the sensors.
When you follow this order, the alerts you see on Day 1 are actual problems, not configuration mismatches.
The "Tagging" Strategy
The most powerful feature in any compliance tool is the ability to filter by tags. Before you connect AWS, ensure your production resources are tagged `Scope: SOC2`. Then, configure the tool to ignore everything else. This single step can reduce your alert volume by 80%.
For more on configuring tools for success, see our Consultant's Guide to Decision Making.
Why Auditors Prefer Scoping
Auditors do not want to see a "perfect" environment where every single test server is locked down like Fort Knox. They know that is unrealistic.
What they want to see is Intentionality.
"We have excluded the `dev-sandbox` account from monitoring because it contains no customer data, as defined in our Data Classification Policy."
That statement is music to an auditor's ears. It shows you understand your risk. Connecting everything and then ignoring the failures shows you are overwhelmed.