In the compliance automation market, there is a fierce debate: Agent vs. Agentless.
Agent-based tools (like Drata's agent) require you to install a small piece of software on every employee's laptop.
Agentless tools (like Vanta's MDM integration) simply connect to your Mobile Device Management (MDM) provider like Kandji or Jamf via API.
The sales pitch for Agentless is obvious: "No software to install! Up and running in 5 minutes!"
But there is a hidden cost to this speed: Evidence Fidelity.
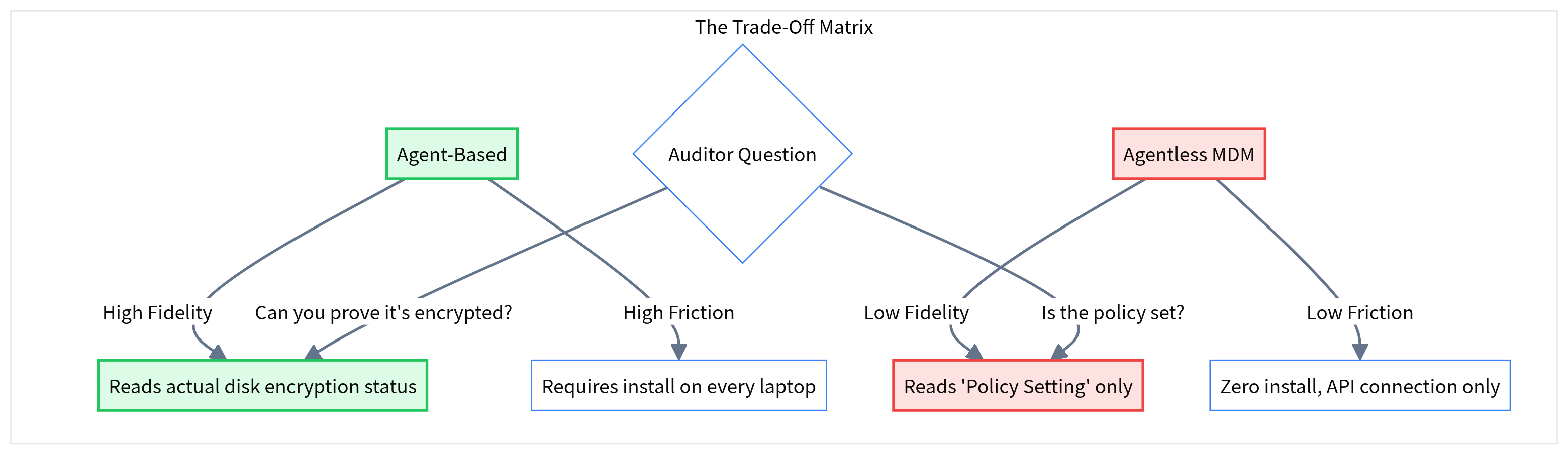
Policy vs. Reality
The fundamental difference lies in what is actually being checked.
Agentless (MDM API): Checks the Policy.
It asks Kandji: "Is the 'Disk Encryption' policy turned on?"
Kandji says: "Yes."
Agent (On-Device): Checks the Reality.
It asks the OS kernel: "Is the disk actually encrypted right now?"
The OS says: "No, the user paused it 10 minutes ago."
In the Agentless scenario, you would pass the check but fail the security reality. In a rigorous audit (especially ISO 27001), an auditor may ask for "evidence of enforcement on a sample device," not just "evidence of policy configuration."
The "BYOD" Nightmare
The Agentless approach falls apart completely with Bring Your Own Device (BYOD).
You cannot force contractors to enroll their personal MacBooks into your corporate MDM (they will refuse). Therefore, an Agentless tool cannot see those devices at all.
An Agent, however, can be installed as a "read-only" app on a personal device to prove compliance (Screen Lock, Antivirus) without taking full control of the device.
If your workforce is heavy on contractors using personal equipment, Agentless is likely a non-starter.
The Hybrid Compromise
The best strategy is often Hybrid. Use MDM (Agentless) for your fleet of corporate-owned devices to reduce friction. Use Agents only for the high-risk or unmanaged devices (contractors, Linux devs) that MDM misses.
For more on architectural decisions, see our Consultant's Guide to Decision Making.
Summary for Buyers
- Choose Agentless if: You have 100% corporate-owned devices, a strong MDM (Jamf/Kandji) already fully deployed, and a standard SOC 2 audit.
- Choose Agent if: You have contractors (BYOD), Linux users, no MDM, or a strict auditor who demands "evidence of state" over "evidence of policy."