In the world of SaaS procurement, the "Integrations Page" is the most deceptive marketing asset.
You see the Jira logo. You see the GitHub logo. You assume: "Great, this tool will automatically pull all my change management evidence."
Then, three months later, your auditor asks for a sample of 25 change tickets to prove that code reviews happened before merging. You open your compliance tool, expecting to find the data. Instead, you find a simple green checkmark next to "Jira Connected."
The tool checked if Jira was online. It did not check if your tickets were compliant. You now have to manually screenshot 25 Jira tickets. The automation you paid for is an illusion.
Shallow vs. Deep Integrations
Not all APIs are used equally. In the compliance automation market, there is a massive gap between "Existence Checks" (Shallow) and "Configuration Audits" (Deep).
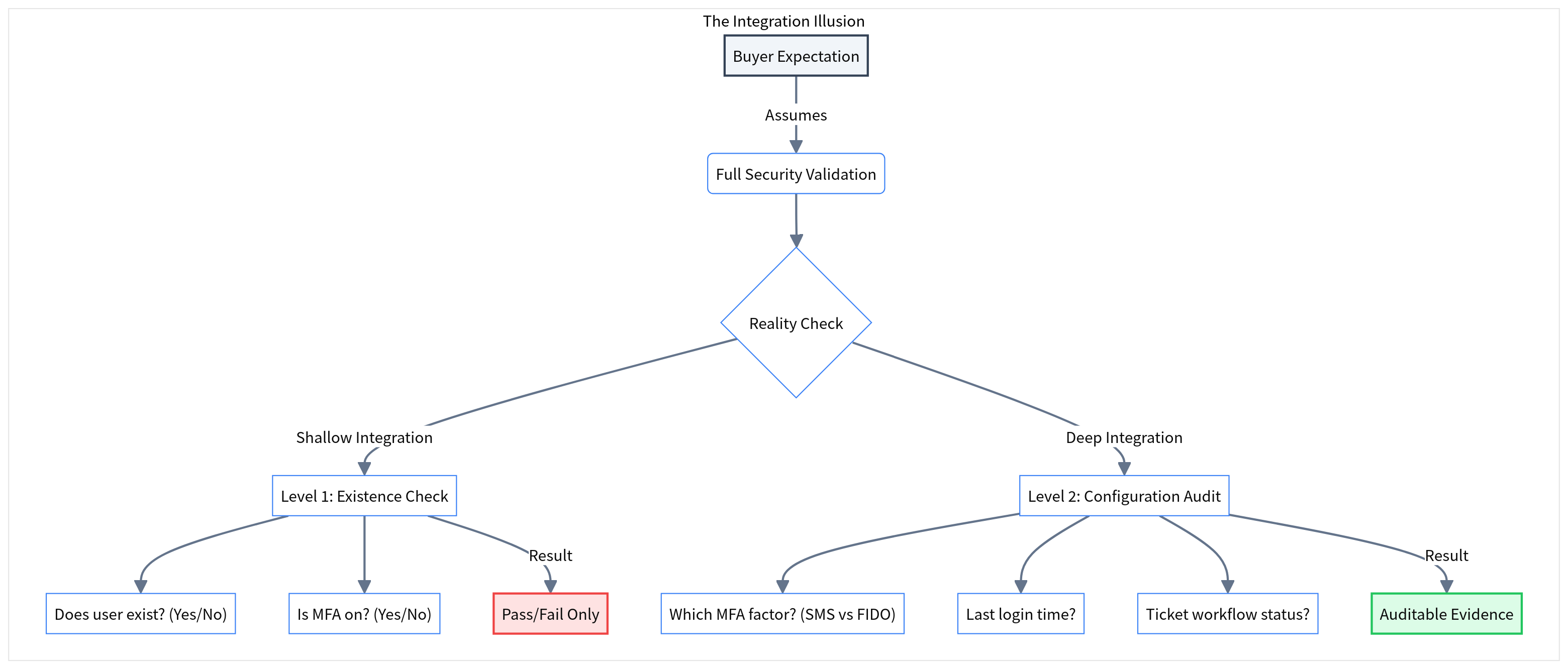
The "Read-Only" Trap
Many tools use the most basic "Read" permissions to minimize setup friction. While this makes onboarding fast (click "Allow" and you're done), it severely limits the data granularity.
For example, a Shallow Integration with an HRIS (like Rippling) might just pull a list of active employees.
A Deep Integration will pull:
- Start date vs. System Access creation date (to prove timely provisioning).
- Termination date vs. Access revocation date (to prove timely offboarding).
- Department metadata (to auto-scope controls).
If your tool only does the former, you will still be doing manual VLOOKUPs in Excel during your audit to prove you revoked access within 24 hours.
How to Test Integration Depth Before Buying
Do not trust the logo wall. During your Proof of Concept (POC), you must perform a "Data Fidelity Test."
- Pick a complex control: Choose something like "Change Management" or "Access Review."
- Ask for the raw evidence: Don't look at the dashboard dashboard. Ask the sales engineer: "Show me the JSON object or the raw export you are pulling from GitHub."
- Verify the fields: Does it include the timestamp of the approval? The ID of the approver? Or just the status "Merged"?
The "Custom" Integration Myth
Vendors often say, "If we don't have the integration, you can use our API to push data." Be warned: Building your own integration is a full engineering project. You will need to write scripts to query your own tools, format the data to their schema, and handle authentication. It is rarely a "quick fix."
For more on evaluating vendor capabilities, refer to our Consultant's Guide to Decision Making.
The Cost of Shallow Integrations
The cost isn't just frustration; it's Audit Fatigue.
When an auditor sees that your automated tool is only checking surface-level data, they will stop trusting the tool. They will revert to "sampling"—asking you to manually prove 10% of your population.
Once an auditor reverts to manual sampling, the ROI of your automation software drops to near zero. You are paying for a tool to tell you everything is fine, while you spend your nights taking screenshots to prove it.