01. Why Compliance Automation is a Critical Decision
In my 15 years of advising organizations on software selection, few categories have exploded as rapidly—or caused as much post-purchase friction—as compliance automation. The driver is clear: trust is the new currency of B2B sales. You cannot close enterprise deals without a SOC 2 report or ISO certification.
Traditionally, achieving this meant hiring a consultant for six months and drowning in spreadsheets. Automation software promises to compress this timeline. But here is the friction point I see repeatedly: organizations confuse "buying a tool" with "building a program."
A poor choice here doesn't just waste budget; it creates a "Compliance Debt" where your automated checks pass green, but your actual security posture is hollow, leading to painful audit findings later. The decision isn't just about speed; it's about the defensibility of your security program.
02. The Evaluation Process: Beyond the Feature List
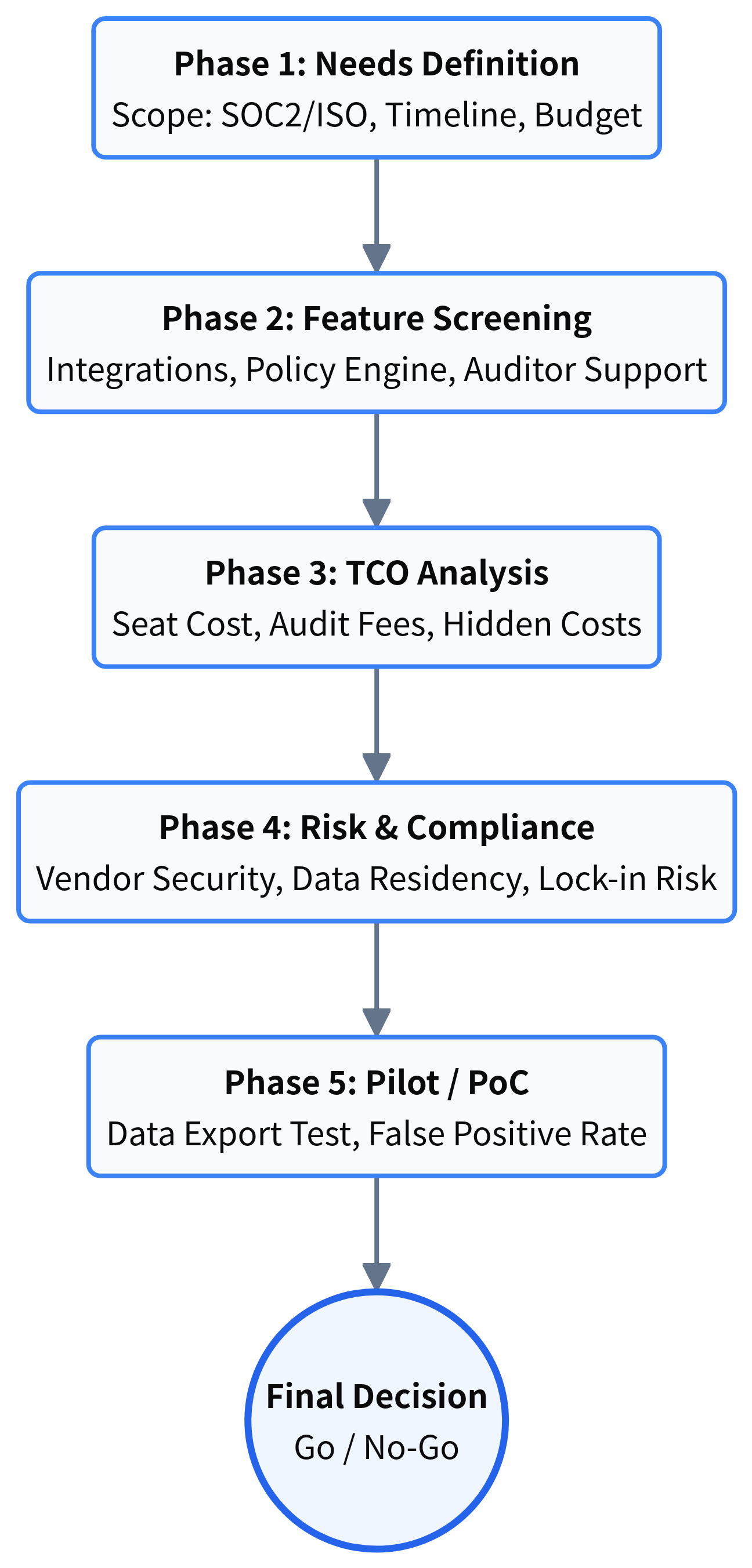
When I walk teams through evaluations, we often scrap their initial "feature checklist" because most vendors check the same boxes (MDM integration, policy templates, AWS scanning). The real differentiators are structural.
The "Auditor-First" Lens
Your software is useless if your auditor refuses to trust its data. I always advise clients to ask: "Does this platform export evidence in a format my external auditor actually prefers, or does it force them into a proprietary workflow they hate?" Friction with your auditor translates directly to higher audit fees.
The "False Positive" Fatigue
In the first month, every alert feels urgent. By month three, if the tool screams because a developer spun up a test instance for 10 minutes, your team will start ignoring it. The quality of the exclusion logic—how easily you can mark something as "safe exception"—is often the deciding factor in long-term adoption.
03. Critical Decision Factors (The Trade-offs)
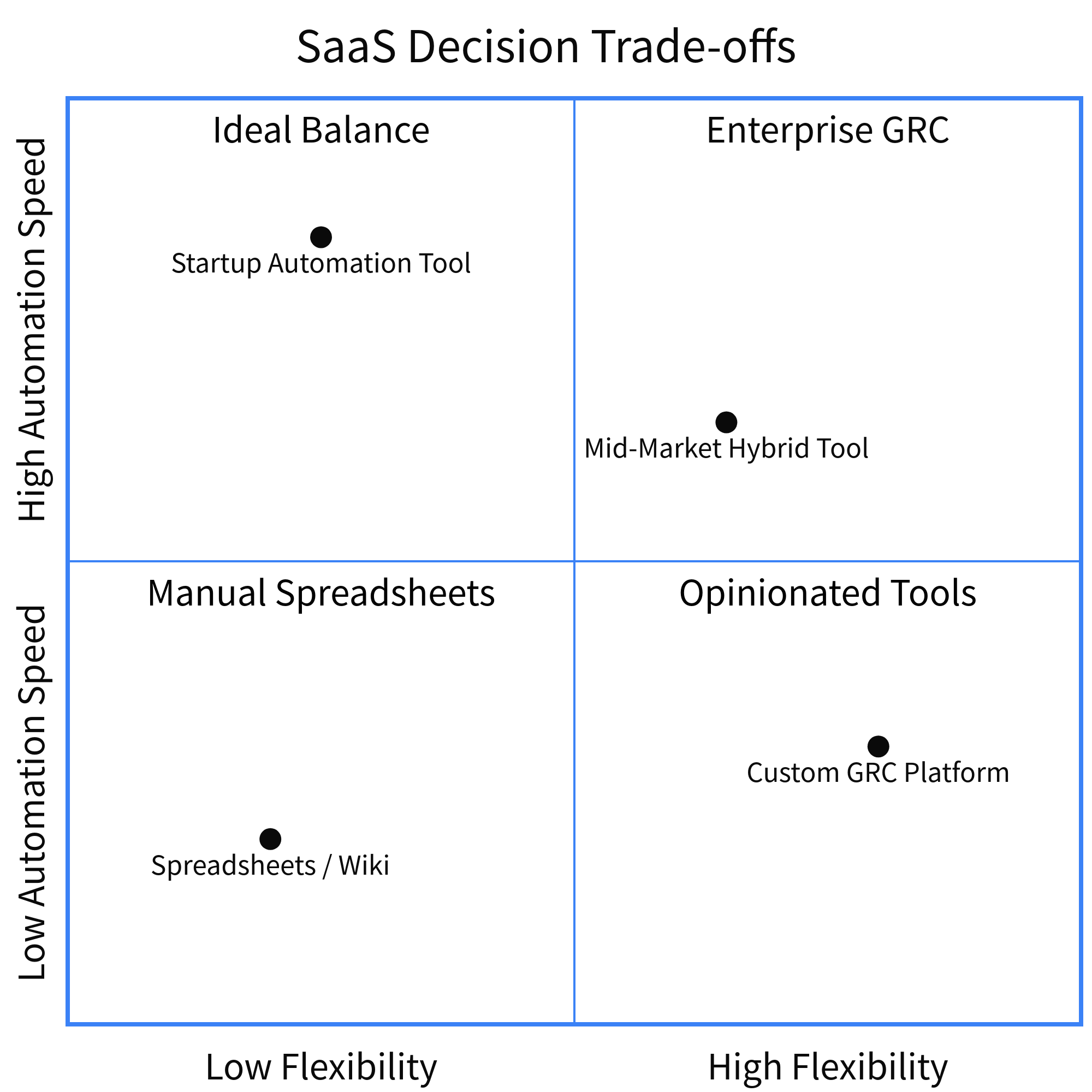
Speed vs. Flexibility
"Opinionated" platforms get you to SOC 2 fast by forcing you to adopt their policies. Flexible platforms adapt to your existing workflows but require more setup time. If you are a 500-person company, "opinionated" tools often break your existing processes.
Continuous vs. Snapshot
Continuous monitoring sounds ideal, but it requires a culture that can handle continuous remediation. If your team can't fix issues daily, a tool that reports daily failures just creates a "Sea of Red" dashboard that demoralizes the team.
04. Scaling Paths: SMB to Enterprise
One size absolutely does not fit all. I've seen Series A startups struggle with enterprise-grade GRC tools, and I've seen public companies crippled by the limitations of startup-focused automation tools.

- The SMB / Startup PathFocus on Template Quality. You likely don't have a CISO. You need the tool to act as a virtual CISO, providing pre-written policies that are reasonable for a small team. The goal is "Minimum Viable Compliance."
- The Scale-Up PathFocus on Integration Depth. You have Jira, Datadog, Jamf, and Okta. If the tool requires manual screenshots for any of these, it fails. The goal is "Efficiency at Scale."
- The Enterprise PathFocus on Custom Frameworks. You aren't just doing SOC 2; you have custom customer commitments. Can the tool track a promise made in a specific DPA (Data Processing Addendum)? The goal is "Unified Control Governance."
05. Global Considerations: Data & Regulations
For organizations operating globally, the "US-Centric" nature of many SaaS tools is a blind spot.
Data Residency & Sovereignty
Does the compliance tool itself store your metadata in the EU? If you are certifying against GDPR or German TISAX, using a US-hosted tool that ingests your employee data can ironically become a compliance violation itself.
Framework Nuance
ISO 27001 is more prescriptive than SOC 2. Some tools are built for the "Trust Services Criteria" of SOC 2 and shoehorn ISO 27001 into that structure awkwardly. If your primary market is Europe or Asia, verify the tool's native support for ISO workflows, not just as an afterthought.
06. Common Questions (FAQ)
Does buying this software guarantee I pass the audit?
No. The software collects evidence; it does not fix security holes. If the tool shows you don't have MFA enabled, and you don't enable it, you will fail. The tool is the mirror, not the makeup.
Can I replace my auditor with this software?
Absolutely not. SOC 2 and ISO certifications must be issued by an independent, accredited CPA firm or registrar. The software is a tool for the auditor, not a replacement of the auditor.
How long does implementation take?
Vendors say "weeks"; reality is often 2-3 months to get to a "clean" state where you are ready for the observation period. The delay is rarely the software—it's the internal remediation of the gaps the software finds.
Final Thoughts: Rational Selection
The best compliance automation tool is the one your team will actually log into.
Don't optimize for the audit you have once a year; optimize for the security operations you live with every day. If a tool makes your engineers hate security because of noisy alerts or rigid workflows, it is a net negative, regardless of how fast it generates a PDF report.
Start with your "Must-Have" integrations. Define your tolerance for changing your internal processes. And always, always test the "Evidence Export" feature before you sign—because that is what your auditor will see.